Information Security Management Systems (ISMS) | An Introduction
Learn how to organize your information security via a management system.
- Articles
- Information Security Management
- Introduction to Information Security Management Systems (ISMS)
Introduction
We hear about it more and more often. Attacks on IT security infrastructure, hacker attacks, and cyber-attacks that can paralyse a business for days. We enjoy many benefits of a more digitised world. But the flip side is that individuals with malicious intentions can potentially gain access to your business operations and critical data.
Thus, it's crucial to take this threat seriously and implement a safety net that can reduce the risk of your business becoming the next target.
The NIS2 Directive is being implemented (the final implementation date for businesses has just been moved to the end of 2024) by a wide range of companies in the EU that are subject to the directive. This includes companies performing critical societal operations or supplying such a value chain. Many companies are required to implement IT and cybersecurity measures to comply with the directive's requirements. Whether or not you are subject to the NIS2 Directive, it's advantageous to consider your IT security. An Information Security Management System (ISMS) is an ideal method to create an overview, identify risks, implement measures, and strengthen your IT security setup.
This article aims to introduce you to what an ISMS is, what it entails, and how you can implement it in your organisation.
What is an ISMS (Information Security Management System)?
ISMS stands for Information Security Management System. It's a framework tool designed for organisations to enhance the security of their information, data, and systems. An ISMS includes various components. From the people in your organisation to technical security measures. It covers a wide area within Governance, Risk, and Compliance (GRC). Below are examples from a typical ISMS framework.
Interested in Governance, Risk, and Compliance (GRC)? Read our in-depth article here.
Policies
Having clear policies and procedures is crucial in any organisation that values data security. The purposes vary. For instance, a deletion policy helps employees understand when and how to delete data. And can be used for onboarding and in ongoing awareness training. Policies and procedures vary in character and method. However, it's essential they are articulated clearly and accessible to the intended recipients.
Controls
A strong control system is the cornerstone of an ISMS. This could be a tailored framework with specific ISMS controls needed for your organisation. Or, it might be based on recognised standards such as ISO 27001. Planning controls, tasks, responsibilities, and documentation is key. Ensuring the plan is followed is crucial.
Use Privacy's free task management to plan and monitor your controls. Learn more here.
Risk Assessments
ISMS adopts a risk-based approach. This involves proactively identifying and documenting potential risks. Implementing security measures to reduce the risk level and hopefully prevent security breaches.
Read more about how to create a risk management framework here.
Monitoring and review
ISMS gives security officers, DPOs, and similar roles a clear overview. And this can be used to strengthen the organisation's security status. This includes documenting where business-critical data is processed. Assess risks in your assets. Set up a control system to ensure ongoing reassessment of risks, policies, and procedures. Then, you have the ability to monitor your organisation's IT security compliance.
What is a DPO and do you really need one?
Is ISMS the same as ISO 27001?
Implementing an ISMS can be done in various ways. It's not confined to a single standard. Yet, ISO 27001 is an internationally recognized standard widely adopted. In Denmark, for example. It's a legal requirement for public institutions to use this framework.
To successfully implement an ISMS, having a strong starting point is beneficial. ISO 27001 provides such a framework, focusing on risk management and controls. This standard guides you in organizing your risk assessments. Helping to establish a solid risk-based foundation in your organization.
ISO 27001 also offers a set of standard controls for organizations to adopt. These controls vary and can relate to legislation, business needs, regulations, or contracts.
You can create your own ISMS framework or follow another, like CIS18. There's no one-to-one equivalence between ISMS and ISO 27001. Yet, it's one of the most used and tested frameworks for information security compliance.
Furthermore a standard like ISO 27001 can also help you complying with GDPR. Standards in compliance frameworks will often have similarities and it will be an advantage for you, to work with them in different areas.
How does ISMS work?
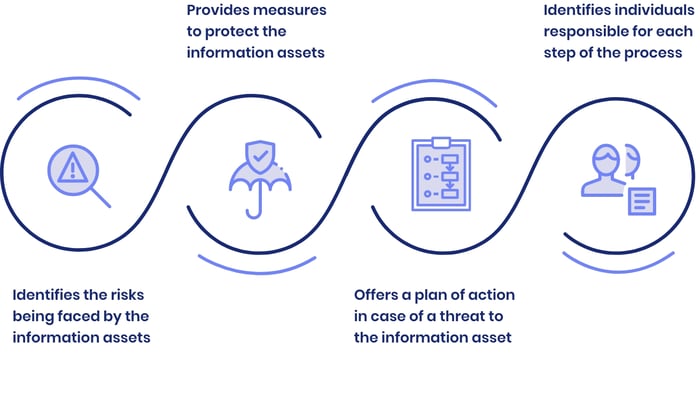
Implementing an ISMS isn't as simple as pressing a button. It's a compliance task rooted deeply within the organisation. It involves defining tasks, implementing policies, procedures, and measures. And educating employees to follow these initiatives. Then it becomes an operational task. Like other compliance areas, ISMS is an ongoing process. It's vital to keep activities up to date. You need to regularly revisit documentation, risk assessments, and to conduct spot checks. In this way, you keep your compliance level with information and cybersecurity measures.
Once you have implemented an ISMS in your organisation, you establish a systematic approach to information security. With ongoing checks and procedures, you can manage your data compliance and risks.
When working with ISMS, aim for the level of implementation that best suits your context. There's no need to aim for the highest level of control implementation. This often leads to unfinished tasks. Instead, make a plan, identify the most critical areas, map out your business, and take a risk-based approach to those areas. It's better to implement ISMS and adhere to procedures and policies in a few critical areas. Than to set an overambitious plan that you can't realistically fulfill.
ISO 27001 is a standard and it is also a standard you can be certified to. It can be beneficial to follow this or a similar standard, as certification is the easiest way to prove that your business is ISMS compliant. Use ISO 27001, ISO 27002 or a similar framework and select the controls that fit your defined plan.
What are the security controls of ISMS?
In an Information Security Management System (ISMS), security controls are critical. Use these to protect your organisation's data. They are categorised into technical and management security controls.
Technical Security Controls
Technical security controls involve the physical and software-based tools used to safeguard data. For example in a manufacturing company, this might include biometric access systems. They ensure that only authorized personnel can enter sensitive areas.
Example of Technical Security Control
An example could be encrypting the communication between machines. This prevents unauthorized insight into the data flows of production. And ensures the integrity of the transmitted information.
Management Security Controls
Management security controls focus on the strategies and policies that govern an organization's security practices. This includes training employees on security protocols. And establishing clear guidelines for data handling.
Example of Management Security Control
For a manufacturing company, this could be regular security audits. These audits ensure that all procedures are followed correctly. And that any security gaps are quickly identified and addressed.
Why does every business need an ISMS?
In a world where data is a critical asset. An Information Security Management System (ISMS) is crucial for any business.
Here are some detailed reasons:
- Data Security: Protects sensitive information of the business and its customers. This could be from cyber-attacks and security breaches. This is essential in an era of increasing cybercrime.
- Compliance: Ensures adherence to relevant data protection regulations and standards. Fx such as GDPR, which is critical for legal compliance and avoiding hefty fines.
- Competitive Advantage: In a tight market, a demonstrated ability to protect customer data can positively differentiate your business. And this can win customer loyalty.
- Loss Prevention: Helps to prevent financial and operational losses. Which can occur due to data breaches.
- Efficiency Gains: By standardizing security processes, the business can achieve greater efficiency. And reduce costs associated with ad hoc security measures.
- Brand Protection: A good reputation is crucial for business success. An ISMS helps to maintain this by avoiding negative headlines about data breaches.
- Continuous Improvement: ISMS offers a structured approach to test, improve, and update security measures. This is necessary to keep up with rapid technological development.
- Clarity in Responsibility: Creates a clear structure for responsibility and roles within the organisation. This helps improve internal coordination and response times to incidents.
- Investor and Customer Confidence: A clear and proven security strategy strengthens the confidence of investors and customers. Ensuring more stable operations.
Implementing an ISMS is not just a technical or compliance exercise. It is a strategic decision that supports the business's overall objectives. And ensures its viability and success in the future.
What are the key benefits of ISMS implementation?
Implementing an Information Security Management System (ISMS) is critical for modern businesses. Here are some of the key benefits that an ISMS can offer your business:
Enhanced Data Security
An effective ISMS strengthens the protective shield around all your data assets. By integrating robust security protocols, you protect not just digitally stored data but also physically stored and cloud-based information. This lays the foundation for a comprehensive security culture throughout the company.
Compliance with Regulatory Requirements
An ISMS is your guide through the maze of regulatory demands. It aids in navigating and adhering to regulations such as GDPR. This is crucial for avoiding sanctions and fines. Especially in highly regulated sectors like financial services or healthcare.
You could also read: GDPR in 2023 - what do you need to be aware of?
Improved Risk Visibility
With an ISMS, you gain a bird's-eye view of the company’s risks. The system enables structured risk assessment. Prioritizing assets based on their vulnerability and value. Allowing for more effective resource allocation.
Cost Savings
Through a detailed risk assessment process, an ISMS ensures that investments in security measures are targeted and necessary. This eliminates wastage and optimizes the budget. By reducing the costs associated with security incidents.
Improved Efficiency and Corporate Reputation
An ISMS streamlines security processes. And it creates a culture where every employee understands the value of data security. This leads to improved efficiency and enhances the company's reputation. Both internally and externally.
Implementing an ISMS is a strategic investment in your company's future. It's not just a mechanism for reinforcing security or achieving compliance. It's a fundamental pillar for the ongoing growth and success of the business.
How to implement ISMS
Depending on your company's level of IT security and compliance maturity, the plan for implementing an ISMS will differ. This also applies to how the implementation is conducted. Especially if you opt to follow a standardised framework such as ISO 27001. Below are some fundamental steps. These may assist you in implementing ISMS within your organisation. Regardless of your starting point and whether you choose to follow a standard or not.
Make a plan
All effective compliance work begins with a well-structured plan. Before implementing ISMS in your organisation, you must create a realistic plan. This plan should reflect your organisation's current state and where implementing an ISMS process is most critical. Starting with a GAP analysis of your organisation's IT and cybersecurity is beneficial.
Involve key stakeholders in the implementation and coordinate a joint plan. Ensure your plan is realistic and tailored to your organisation. Consider resources in terms of finances and time. Assess which competencies you possess and whether there is a need for external resources during the process.
It's wise to engage your colleagues early in the process. Education should be part of your plan. The more your colleagues are involved, the faster the process will become a natural part of your organisation.
Choose a tool
As you've read through the article, ISMS encompasses various elements and tasks. Having a tool on hand when implementing ISMS can be advantageous. There are many types of tools for different facets of ISMS. At a minimum, you should choose a tool that provides an overview. This help you to monitor the progress of your plan. And keeps your documentation organised throughout the implementation.
.legal offers the Privacy ISMS tool to assist in your process. Learn more about Privacy ISMS here.
Choose a framework
Earlier in the article, we touched upon different frameworks that can support your ISMS process. You have the option to create your own framework based on the tasks you deem necessary. But you could also opt to follow a standard, such as ISO 27001. Consider if you wish to use a standard framework. Then, it's essential to assess which parts of the framework you intend to implement. It's rarely advisable to adopt all tasks and activities from a given framework outright. Doing so could become overwhelming and include activities irrelevant to your specific organisation.
Map assets and processes in the organisation
When you start implementing your ISMS compliance, the initial step involves a thorough mapping exercise. ISMS focuses on IT and cybersecurity. You will often identify the most critical areas within your IT landscape. This could include an IT system used within the organization or a sensor used in the warehouse. Consider where your organization connects to the network. It will be a good strategy to begin by mapping these areas.
This mapping is also referred to as business data mapping. And this should also give you an overview of your suppliers. This is crucial for later conducting audits and ensuring their compliance as well.
You can also read more about Privacy's data mapping functions here.
Identify and document potential risks
After mapping out the various entities within your organization, it's time to conduct risk assessments on these. It's essential to consider each entity or the processes in which the entity is involved. Ask yourself: What does the entity do? What data does the entity process?
Begin by developing a range of threat scenarios and scenarios. Review these in relation to each of your entities. Then, assess the consequences if a particular threat scenario becomes a reality, and identify the likelihood of its occurrence.
This step will provide you with a risk score for each system, which is crucial for your continued work with ISMS. It helps you identify where it is most critical to focus your efforts.
Implement safety regulations
Security measures are essential in reducing risks. They can be both technical and organisational. After identifying the most significant risks in your organisation, it makes sense to focus on the entities or processes where the risk is highest.
Consider which measures could effectively mitigate the risk in those scenarios. Sometimes, stronger technical solutions, such as two-factor authentication or a firewall, can be the answer. Other times, it may involve organisational measures, like policies that train employees on how to securely leave their workstations.
Educate your colleagues
Compliance and the implementation of an Information Security Management System (ISMS) require a collective effort across the organisation. Effective compliance is best achieved when it is deeply embedded in the organisation's culture. Your colleagues must understand and follow the plan and framework you have implemented. Without their awareness and active participation, the risk of security breaches remains high.
To ensure broad engagement, consider how you can make policies, procedures, and your security plan easily accessible to all employees. This might be through an internal platform where materials are easy to find and review. It's also advisable to introduce a process where employees confirm they have reviewed and understood the relevant training materials. This ensures everyone is informed about how to act following ISMS requirements.
Additionally, include security training as a standard part of the onboarding process for new employees. This ensures they are equipped with the necessary knowledge and understanding from the outset to contribute to the organisation's security culture. By making compliance an integral part of everyday life in your organisation, you strengthen the foundation for secure and responsible business operations.
Operation and improvenments
Once you have implemented your ISMS, it is crucial to consider how it will be managed and maintained going forward in an operational context. Therefore, plan an annual cycle of activities that need to be carried out throughout the year. Ensure that tasks are properly anchored with the right individuals and that these individuals are reminded at the appropriate times. Additionally, develop a plan for continuous improvements in areas you have identified as needing extra attention and further measures. This strategic approach ensures your ISMS is effectively maintained and evolves to meet the demands of your organisation and the changing landscape of information security.
How .legal Can Enhance Your Information and Risk Management and Compliance
At .legal, we specialise in compliance. We offer a compliance platform designed to aid you with your documentation tasks. Named Privacy, this platform comprises various modules, including Privacy GDPR and Privacy ISMS. The latter module is tailored to support you in the implementation and operation of your ISMS.
Privacy ISMS provides access to modules that you can use for:
- Mapping of business processes and identification of units/systems
- Risk management and the creation of risk assessments
- Planning of an annual cycle and tasks, including associated frameworks
- Storage of policies and procedures
- Recording of incidents and security breaches
- Management of suppliers and contracts
Thus, Privacy ISMS offers you a tool that aids in monitoring your ISMS implementation and its subsequent operation.
Interested in trying Privacy ISMS? You can start with the platform entirely for free today.


.jpg)


.jpeg)

.jpg)
.jpg)



.jpg)

-1.png)



.jpeg)








.jpg)

Info
.legal A/S
hello@dotlegal.com
+45 7027 0127
VAT-no: DK40888888
Support
support@dotlegal.com
+45 7027 0127
Need help?
Let me help you get started

+45 7027 0127 and I'll get you started
.legal is not a law firm and is therefore not under the supervision of the Bar Council.