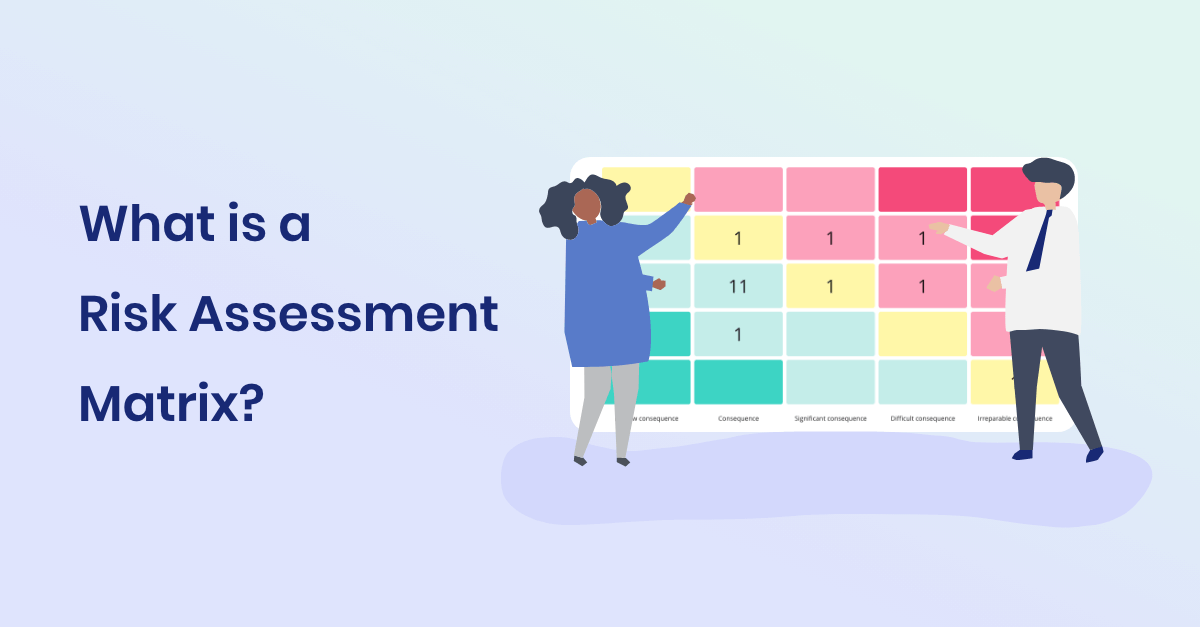
GDPR Risk Assessments
Learn all about risk assessments and get examples of how to conduct risk assessments.
TL;DR – Key takeaways on GDPR Risk Assessments
-
Take a risk-based approach to stay ahead of problems.
GDPR isn't just about documentation – it's about identifying where personal data could be at risk and acting before incidents happen. -
Use a clear and structured framework for your assessments.
A good framework helps you map data activities, create realistic threat scenarios, and assess risks based on both likelihood and impact. -
Let DPIAs and risk matrices bring clarity and consistency.
Data Protection Impact Assessments and visual tools like risk matrices support informed decisions and help you justify your approach. -
Keep your risk documentation updated and relevant.
Risks change over time. Regular reviews ensure that your assessments reflect current practices, systems, and legal requirements. -
Simplify the process with the right tool.
A GDPR platform like .legal compliance platform gives you predefined scenarios, built-in guidance, and automation – saving time and reducing complexity.
Introduction
The General Data Protection Regulation (GDPR) is a crucial aspect of data protection for businesses in the EU. You might have already taken significant steps in your GDPR journey.
Perhaps you've compiled your Article 30 record, updated your privacy policy on your website, and have full control over your cookies. And maybe you have an annual plan to keep your documentation up to date.
Yet, risk assessment remains a challenge for many. We know that carrying out risk assessments on your data processing activities can seem overwhelming for many people. This often stems from a lack of an effective framework to guide the process. However, a risk-based approach to GDPR is extremely important. It enables you to act proactively in your work with personal data.
Much like other GDPR tasks, a solid framework can actually make risk assessments more manageable. In this article, we dive into the critical elements of a risk assessment. Why it is important, and offer suggestions on how such a framework can be designed. Toward the end of the article, you'll also find a concrete example of what a risk assessment could look like.Read also: What does Governance, Risk and Compliance mean?
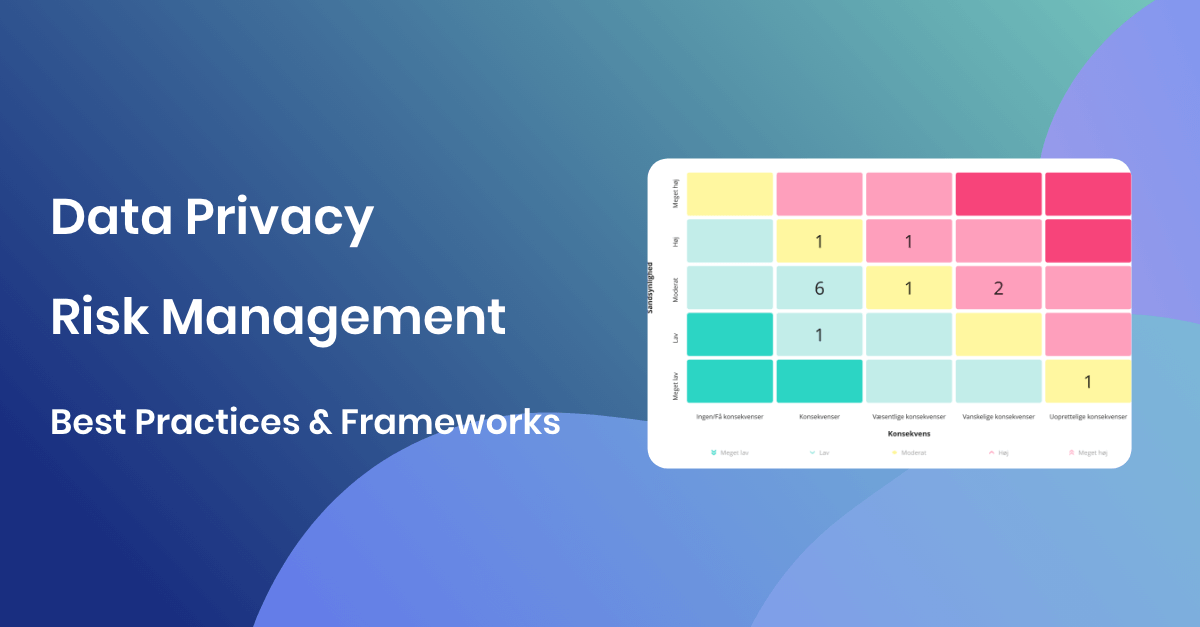
Highlighted Data Privacy Risk Management Processes
Managing data privacy risks is not just a legal necessity but a cornerstone for building trust with your stakeholders. Below, we unpack key components of an effective data privacy risk management process that you should have in place.
A. Proactive Assessment of Security Risks
Begin by actively identifying and assessing potential threats to your data. A comprehensive framework guides you through various aspects of the risk assessment process. Mapping out processing activities involving personal data is the first step. This sets the stage for creating risk scenarios to visualize potential threats. The proactive nature of this exercise allows you to prevent incidents before they occur.
B. Strengthening Data Privacy and Privacy Programs
Strengthening your data privacy goes hand-in-hand with enhancing your overall privacy programs. It's not just about ticking off compliance boxes. It's about instilling a culture where data protection is integral to all operations. The objective is to make well-informed decisions without falling into the trap of 'analysis paralysis.' A structured framework enables you to integrate data protection measures effectively. This helps ensure that privacy becomes a focal point in your organizational activities.
C. Data Protection Impact Assessments (DPIAs/PIAs)
Data Protection Impact Assessments (DPIAs) or Privacy Impact Assessments (PIAs) are essential tools for measuring the effectiveness of your privacy programs. They add a layer of scrutiny, helping you understand the real risks involved in each data processing activity. By using detailed information from each specific processing activity, DPIAs enable you to comprehensively understand the risks involved and act accordingly.
D. Implementing Data Minimization and Retention Policies
Data minimization and crafting precise data retention policies are fundamental practices in reducing risks. Limit data collection to only what is necessary for the designated purpose, and establish clear guidelines on how long the data should be retained. These practices minimize the surface area for potential threats and help you align with GDPR's principle of 'data minimization.'
E. Monitoring Privacy Program Deadlines and Trends
Stay ahead of the curve by continuously monitoring your privacy program's deadlines and being attuned to industry trends. Whether it's compliance audits or updating your policies, keep track of when and what needs to be done. Paying attention to the evolving privacy landscape will allow you to adapt your strategies effectively.
In summary, an effective risk management program must be methodical and in-depth, offering a systematic approach to assessing personal data risks.
Effective risk management is the bedrock on which a resilient data privacy program is built. Therefore, a nuanced approach that blends legal compliance with a proactive privacy culture is the most effective strategy.
Data Risk Assessments
A GDPR risk assessment is a review of the personal data an organization processes. With the purpose to identify and evaluate the risks associated with data handling. The main aim of GDPR is to ensure the protected handling of personal data. This means you need to be clear about what personal data you're processing and why. Which you might already have documented within your data processing activities. Yet maintaining data protection also requires a risk-based approach to the data you handle.
Let's illustrate this with an example. Consider the difference in data security based on how you store information. Storing your employees' data on an open network poses a higher level of risk. On the other hand, implementing security measures like access control dramatically lowers this risk.
Do you need assistance in terms of making Risk Assessments? Try our free Privacy tool
Data Risk Management Best Practices
Doing a good GDPR risk assessment is really important. It helps you protect personal data and meet the rules set by the law. While there is detailed guidance from the Data Protection Authority, we offer a step-by-step guide. This guide aims to make the process easier for you.
-
Identifying Areas of Data Processing: Start by finding out where in your organization personal data is being processed. Also, determine what specific types of information you are handling. Keep in mind, documenting this is already a requirement under GDPR. This is especially true as it's part of your official data processing activities and records.
-
Understanding Threats to the Data Subject: It's important to think about and identify threats that could come from your data processing work. Use the framework you've chosen to outline possible threat scenarios. Make sure these scenarios are relevant to your organization.
-
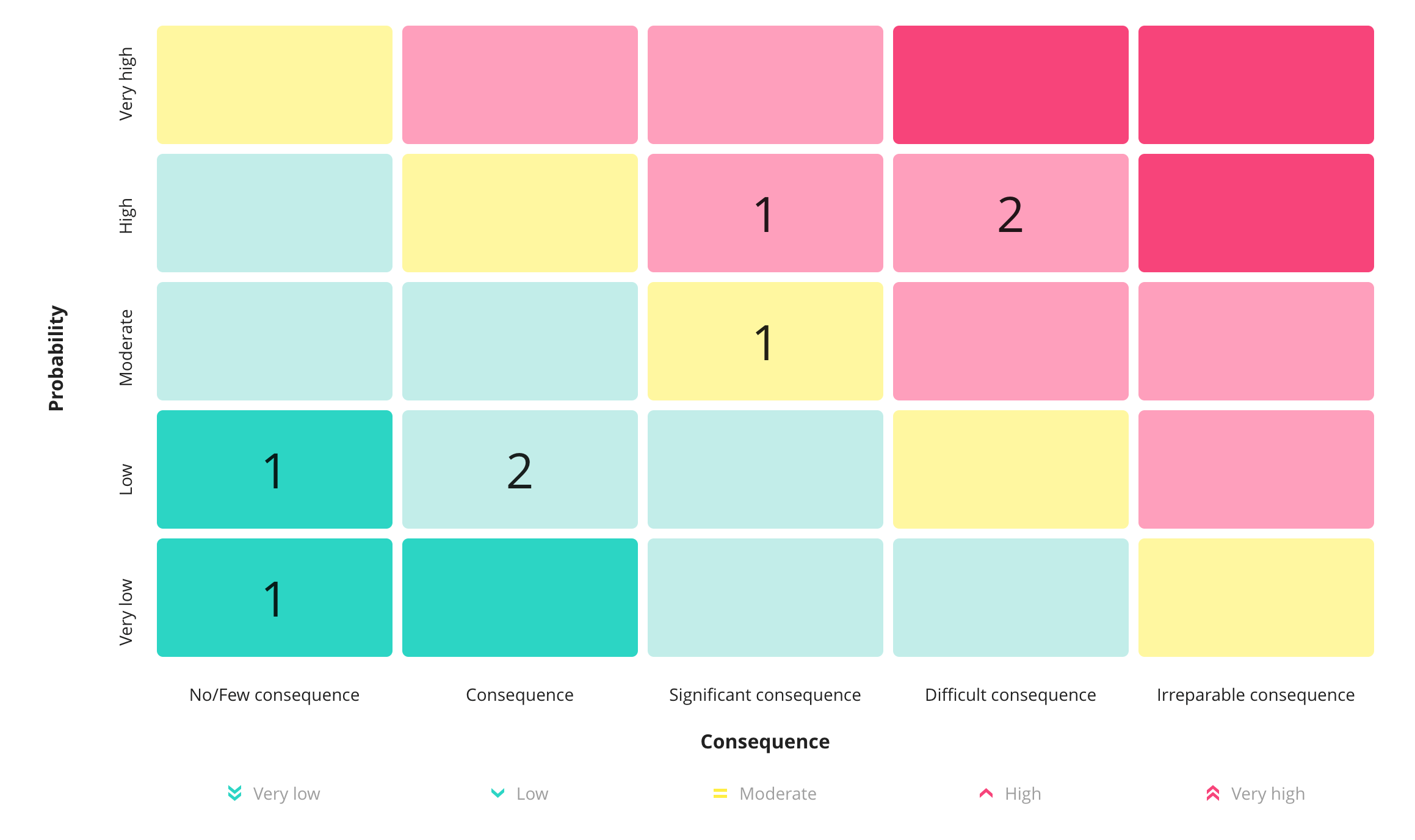
Risk Calculation: Look at each threat you've identified. Then assess how much risk it poses to your data processing. Consider two things: how likely is this to happen, and what could be the impact on the person whose data it is. Using these two elements, you can create a risk matrix. This will help you determine a risk score, which is also recommended by the Data Protection Authority.
-
Highlight High-Risk Areas: After assessing all your data processing tasks, focus on the high-risk areas. It's good to know your organization's general level of "risk tolerance." But pay special attention to any activity that has a high or very high risk level.
-
Mitigate Risks and Implement Security Measures: In high-risk areas, put in place specific security steps. You can either lessen the possible impact of a threat or make it less likely to happen. After you've done this, keep updating your risk assessment. This ensures that what you're doing is actually making a difference.
Justify your choices in the Risk Assessments: Consequence and Properbility Explored
When you explore the details of your data processing activities, performing risk assessments is crucial. It's important to articulate your reasoning for each assessment clearly and precisely. This serves several key purposes:
- Self-Understanding: Having clear justifications ensures that you're applying a consistent approach to decision-making. It also allows you to reflect on your choices later.
- External Communication: Sometimes external parties may ask for details about your risk assessments. This could be a DPO, regulators, or stakeholders. Providing a clear argumentation helps them understand your assessment process.
Data Privacy Risk Management Frameworks
Risk assessment can often seem like a complex task. But using a well-developed framework can simplify the process. It can also improve the accuracy of your assessments. This framework should serve as a systematic guide through the many aspects of the risk assessment process.
Let's go through the different steps a framework like this can include:
Risk Assessment Example
Based on the above framework, we will in this article create a simplified example of a risk assessment. This is made on a data processing activity called "Payroll." This process includes information about our employees. And the data handled are in connection with the payment of salaries.
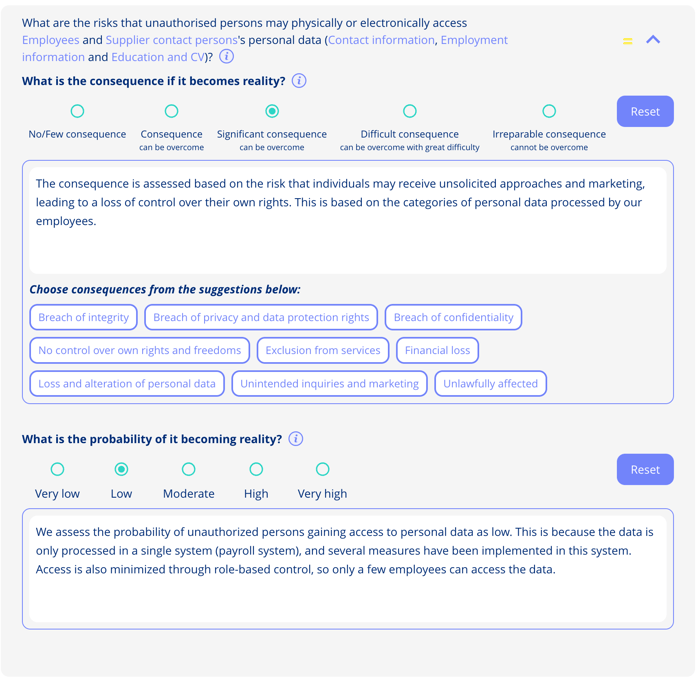
Scenario 1:
"What is the risk of unauthorized persons gaining physical or electronic access to employee personal information (Contact information, Employee information, Financial information, Social Security Number)?"
Consequence:
Assessment: 3 (Significant consequences, can be overcome)
Reasoning: The consequence is assessed based on the risk that individuals may receive unsolicited approaches and marketing, leading to a loss of control over their own rights. This is based on the categories of personal data processed by our employees.
Probability:
Assessment: 2 (Low)
Reasoning: We assess the probability of unauthorized persons gaining access to personal data as low. This is because the data is only processed in a single system (payroll system), and several measures have been implemented in this system. Access is also minimized through role-based control, so only a few employees can access the data.
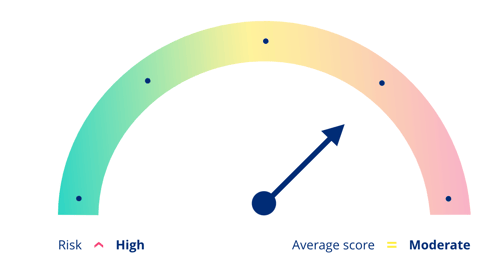
Risk: Moderate
Scenarie 2:
"What is the risk of personal information (Contact information, Employee information, Financial information, Social Security Number) being stored in phased-out IT systems?"
Consequence:
Assessment: 2 (Consequences, can be overcome)
Reasoning: The consequence of this becoming a reality is that there would be a prolonged period during which personal data could be hacked and exposed to cyber attacks, etc.
Probability:
Assessment: 1 (Very Low)
Reasoning: We only perform our payroll process in a single central system that is still active and updated regularly according to our IT security policy. When our previous payroll system was phased out 5 years ago, data was first pseudonymized and later deleted as documented and validated.
Risk: Very Low
The risk assessment for the data processing activity "Payroll" is set to Moderate.
Wrapping up
Navigating the GDPR terrain can sometimes feel like an overwhelming task. But with a robust framework at hand, the complex landscape transforms into a structured and more manageable process. Our example focuses on "Payroll." In this case, we use carefully crafted risk scenarios. We also maintain a methodical record. Together, these elements make the risk assessment process more transparent.
At .legal, we offer the product "Privacy". A platform specifically designed to assist organizations with GDPR compliance. With "Privacy," users can not only benefit from predefined risk scenarios and a comprehensive catalog. They can also easily integrate their own data and processes. This ensures a holistic approach to risk management within the framework of GDPR. You can read more about Privacy here.
Start using Privacy today - you can create your own platform in two minutes, and it is free.
The images used in this article are from the Privacy platform's risk module.
GDPR Compliance Software


.jpg)


.jpeg)

.jpg)
.jpg)



.jpg)

-1.png)



.jpeg)








.jpg)

Info
.legal A/S
hello@dotlegal.com
+45 7027 0127
VAT-no: DK40888888
Support
support@dotlegal.com
+45 7027 0127
Need help?
Let me help you get started

+45 7027 0127 and I'll get you started
.legal is not a law firm and is therefore not under the supervision of the Bar Council.