What is... Information Security Risk Management.
Learn about ISRM in this article and how to apply it in your Information Security Governance.

Introduction
Information Security Risk Management, abbreviated as ISRM, involves managing risks related to information security. E.g., IT systems and cyber threats. Risk management goes hand in hand with compliance requirements and governance in your business. Making it a cornerstone of business operation. Information security is becoming increasingly relevant with the introduction of more sophisticated digital technologies. For example the rapid adoption of AI in everyday business operations.
Read more: What is Governance, Risk and Compliance?
This article aims to unfold the concept of information security risk management. We will discuss what it is and why it's important. We will look at the stages you should be aware of concerning information security risk. And we suggest a framework and examples of how you can conduct your risk assessments.
When discussing risk assessments related to IT security, we focus on the threats to your digital infrastructure. Yet, there is often overlap with other relevant risk assessments carried out within the organization. This could include assessments arising from compliance requirements, such as the GDPR.
What is information security risk management?
Information security is becoming increasingly relevant. This is due to a rising number of hacker attacks. And unwanted third parties who illegally access sensitive and business-critical data. It's also more common for systems to be shut down, with "attackers" demanding a ransom to release them. This can be costly due to the inability to conduct business and damage to business reputation.
As our daily lives become more digitalised and more activities take place online, the risk of these attacks increases. Therefore, it's likely that we will see more frequent and advanced attacks in the future. How can a business protect itself against these threats? It's unrealistic to think that a business can be 100% secure. There will always be vulnerabilities, even in the strongest security wall. And there will always be a risk of human error allowing unwanted guests access. However, it is possible to bolster security to minimise risk. This is where information security risk management comes into play. By conducting a risk assessment, we identify potential risks to act proactively before damage occurs. This allows for the identification of vulnerabilities in the security net. And the implementation of measures to patch these gaps before a security breach occurs.
Thus, information security risk management becomes a crucial part of business operations, enhancing security and peace of mind against large-scale hacker attacks.
Read more: What is a Information Security Management System (ISMS)?
Why is risk management important for information systems security?
Risk management in information systems is key to any business's security strategy. It brings essential benefits that not only ensure the company's data integrity but also strengthen its overall security stance:
-
Preventing data breaches: By carefully identifying and reducing risks, businesses can effectively prevent potential security incidents leading to serious data breaches. This is crucial as cyber attacks become more sophisticated.
-
Protecting company assets: Security risk management is vital for protecting both physical and digital assets. This includes everything from customer data to the company's reputation, crucial for its survival and success.
-
Compliance with laws: ISRM is needed to ensure the company follows relevant laws and standards. Including GDPR. This helps minimise the risk of legal consequences and fines due to non-compliance.
-
Boosting customer trust: A strong and transparent information security policy increases customer trust. So they know that their data is handled with the utmost responsibility. This is essential for building and maintaining long-term customer relationships.
-
Effective risk management: By adopting a proactive approach to risk management, companies can adapt to new threats. This ensures continuous operation and reduces potential losses from unforeseen security events.
Moreover, a well-implemented ISRM process contributes to a culture of security awareness among employees. This is essential for minimising the risk of internal security threats. By continuously assessing and updating security measures, companies not only secure their current safety status but also their future resilience against cyber threats.
Integrating risk management as a core part of the security measures for information systems is thus not just a strategic advantage. It's a necessity for ensuring the company's long-term success and stability in a digital era.
What is the difference between information security risk and cyber risk?
When managing risks, assessments, and mitigation, it's crucial to be aware of the context. Information security and cybersecurity often overlap. It can be challenging to pinpoint the differences between the two areas due to their natural overlaps. Yet, consider performing risk assessments for both the information and cyber aspects.
Read more: What is the difference between Information Security and Cyber Security?
Risk assessments in information security
Information security has a broad focus. Your risk assessment in this area will reflect that. You focus on the bigger picture of the risk level for the organization's information as a whole. This includes both physical and digital information. There might be a focus on different types of information, like business and personal data. This means there could be overlaps between your information security risk assessments and your GDPR risk assessments.
Many organizations use a framework like ISO27001 to assess their information security risk.
Risk assessments in cybersecurity
Cybersecurity is a specific area within information security. It focuses on concrete threats to your digital infrastructure. The concept of cybersecurity has become more prevalent as the world becomes more digitalised.
Cybersecurity risk assessments focus on specific threats to your digital infrastructure. This includes systems, servers, and networks. A cybersecurity risk assessment will typically concentrate on threats like phishing and hacker attacks. It also covers measures to protect the digital infrastructure, like access control and firewalls. Many organizations follow a framework like ISO27002 to identify their cybersecurity risk assessments.
Information security risk management framework
As mentioned earlier in the article, knowing where to start with your information security risk assessments can be challenging. Therefore, using a framework that provides overarching guidelines and helps you identify the areas to consider in your risk assessments can be beneficial. In some countries, national authorities may require organisations within specific sectors to adhere to certain standards. For example, public organisations in Denmark must follow the ISO27001 and ISO27002 frameworks.
The most widespread frameworks are ISO27001-ISO27002 and NIST. While NIST is a US-based framework, the ISO standards operate internationally. This doesn't mean that NIST can only be used in the USA. It can also serve as an effective framework for European businesses.
By adhering to the ISO27001 framework, you also have the opportunity to become certified. This can provide third-party verification that you comply with this well-known framework. Which can be a significant advantage. Especially when documenting information and cybersecurity to, for example, customers and partners. Conversely, the NIST framework does not offer a certification option.
The NIST framework is available at no cost, but if you wish to use an ISO standard, you must purchase a license. This requires contacting your national provider of the standard. In Denmark, this is Dansk Standard.
What are the stages of ISRM?
Information Security Risk Management (ISRM) splits into four main stages. Each phase naturally leads to the next. You can't jump through the stages as all steps are key to your risk management process. This section will go over each phase in your risk assessments and what to watch for.
Identifying and Mapping Your Information Assets
The first step is identifying and mapping your information assets. It helps to note if it's a asset/process needing a risk assessment for information security and/or cybersecurity. Also, consider if the asset should be checked against compliance requirements like GDPR or NIS2.
You can do your risk mapping through data mapping, thinking about areas like:
The asset itself and its specs. What's the asset used for? Is it linked to a network? Are there links to other assets? What security measures have you set up for the asset? You might also look at the organisation's work processes, where systems (like IT) are part of the workflow.
Read more: Start your data mapping with our simple data mapping tool
Risk Assessment
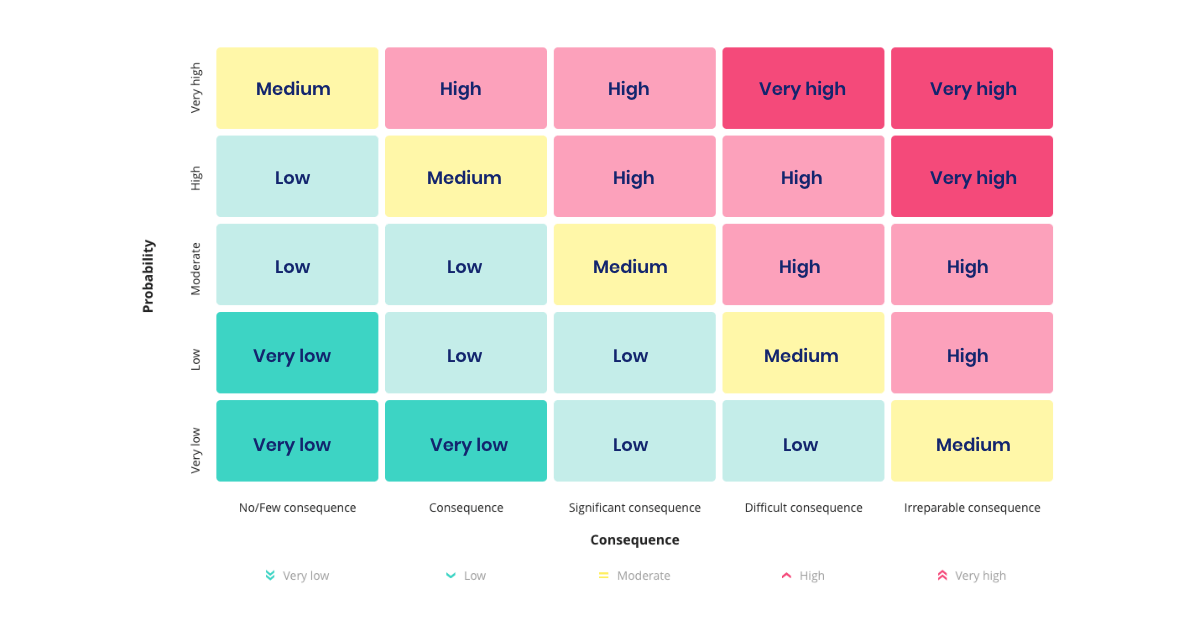
Now, assess the risk for each mapped asset or process. For each risk assessment area (information security or cyber), set up broad risk and threat scenarios. Use these to evaluate each asset or process. Think about the impact and likelihood of each scenario. With these assessments (and their reasons), you can make your risk score by putting them in a risk matrix.
Read more: What is a Risk Assessment Matrix?
Risk Management
With the risk assessments done, you get an overview of all units or processes and their risk level. This gives a visual on where vulnerabilities are, letting you act on them. If you put all your risk assessments into a risk matrix, a rule of thumb is to first deal with the "red" risks. Consider why they score high and how to lower this score. Organisations' risk appetites vary, and some look at "yellow" risks too.
Ongoing Updating and Reporting
Regularly revisit your risk assessments. The world changes, and so will your assessments. Changes might come from within, like a new system or process. Or from outside, due to new compliance demands or laws you must follow. Also, those you're protecting against get more advanced in their methods, meaning new threat scenarios might emerge for your risk assessments.
Finally, it's vital to document your risk assessments and management plans at all times. This reporting is crucial at a management level, making risk a key agenda item and ensuring identified risks are taken seriously. Reporting can also be used externally, like during inspections or certification processes.
Because of this, it can be your advantage to make your risk assessment work as part of your annual compliance wheel.
Ownership & stakeholders in the risk management process
In any strong risk assessment process, there will be various roles and responsibilities. This is because the knowledge needed to perform in-depth risk assessments, management, and decision-making is seldom found in just one person.
In a risk management process, there will often be both:
-
A process and/or system owner
-
A risk owner
-
And management involved
Furthermore, it's natural for a data protection officer or an information security expert to define the overarching frameworks for the risk assessments. Such as which threat scenarios to evaluate.
The process or system owner should be involved in the risk assessment of the systems and processes they own. It's usually here the necessary knowledge about how the specific asset is used, which can provide relevant data for the risk assessment. Typically, this person will also assist in implementing measures in the risk management phase to reduce risks.
The risk owner could be the same as the process or unit owner, but it could also be another party, like the DPO. The important thing is to appoint a risk owner to ensure that any identified risks are managed and acted upon.
Read more: What is a Data Protection Officer (DPO)? And do I really need one?
Management must also be involved in the risk assessments. They don't necessarily need to delve into the details of each risk and threat scenario. But if the risk owner presents them with a series of high risk assessments, management should be able to make a final decision regarding the further plan.
In this way, there can naturally be many parties involved in a strong risk assessment process. ISRM thus becomes a collaborative exercise, where several colleagues contribute their efforts to collectively reduce the risk of information and cyber attacks.
GDPR Compliance Software


.jpg)


.jpeg)

.jpg)
.jpg)



.jpg)

-1.png)



.jpeg)








.jpg)

Info
.legal A/S
hello@dotlegal.com
+45 7027 0127
VAT-no: DK40888888
Support
support@dotlegal.com
+45 7027 0127
Need help?
Let me help you get started

+45 7027 0127 and I'll get you started
.legal is not a law firm and is therefore not under the supervision of the Bar Council.