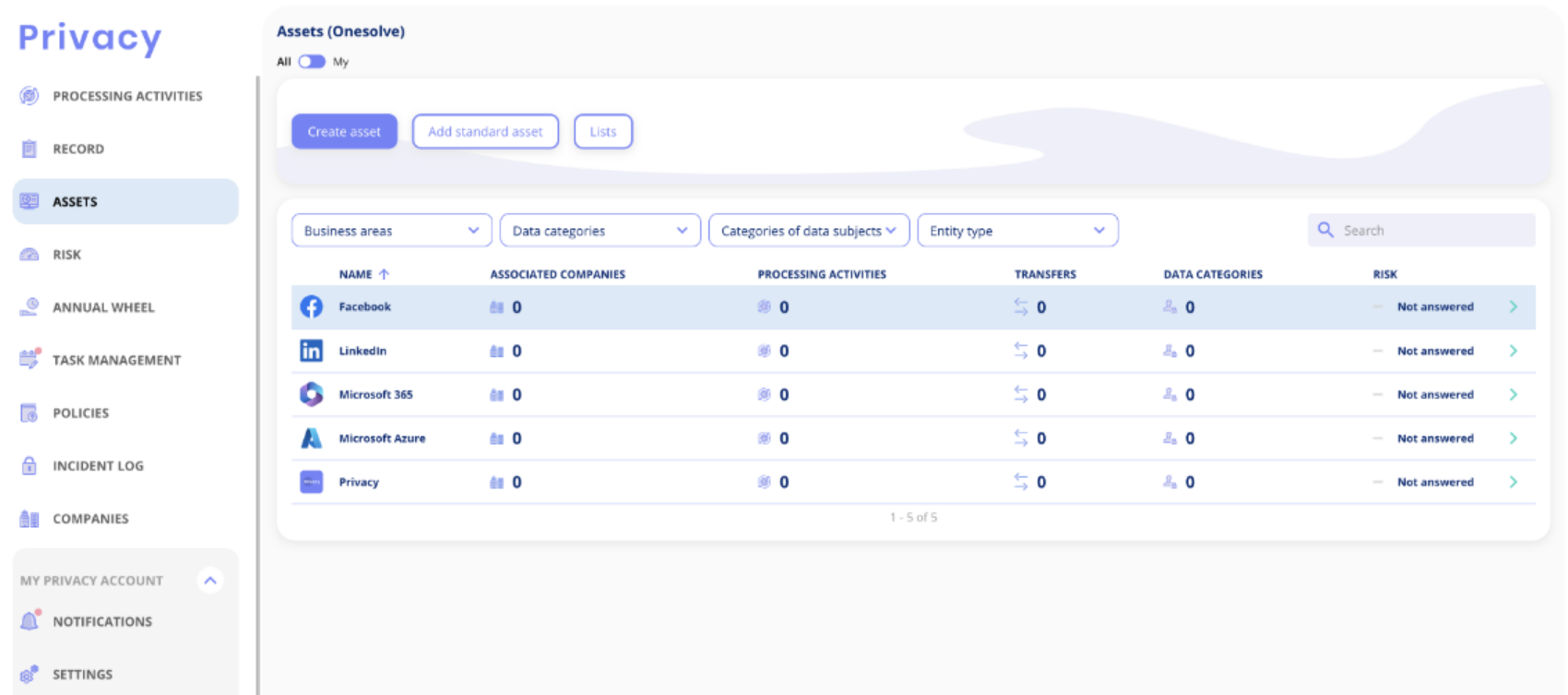
- Product
- .legal platform
- Information Security

Comprehensive Features to Ensure Security and Compliance
Our platform is built to provide you with the tools necessary to protect your critical assets and meet regulatory standards. Whether you are focused on cyber threats, vendor management, or complying with NIS2 and ISO standards, we’ve got you covered.
-
Risk Management at the Asset
LevelIdentify and mitigate risks specific to each asset, ensuring proactive protection against cyber threats. -
System Mapping
Map out and assess your IT infrastructure, highlighting dependencies and potential vulnerabilities. -
Vendor and Contract Risk Management
Track and assess risks associated with third-party vendors and ensure that all contracts are compliant with security standards. -
Tasks and Controls for NIS2 and ISO Standards
Automate and manage compliance tasks in line with NIS2, ISO 27001, and ISO 27002.
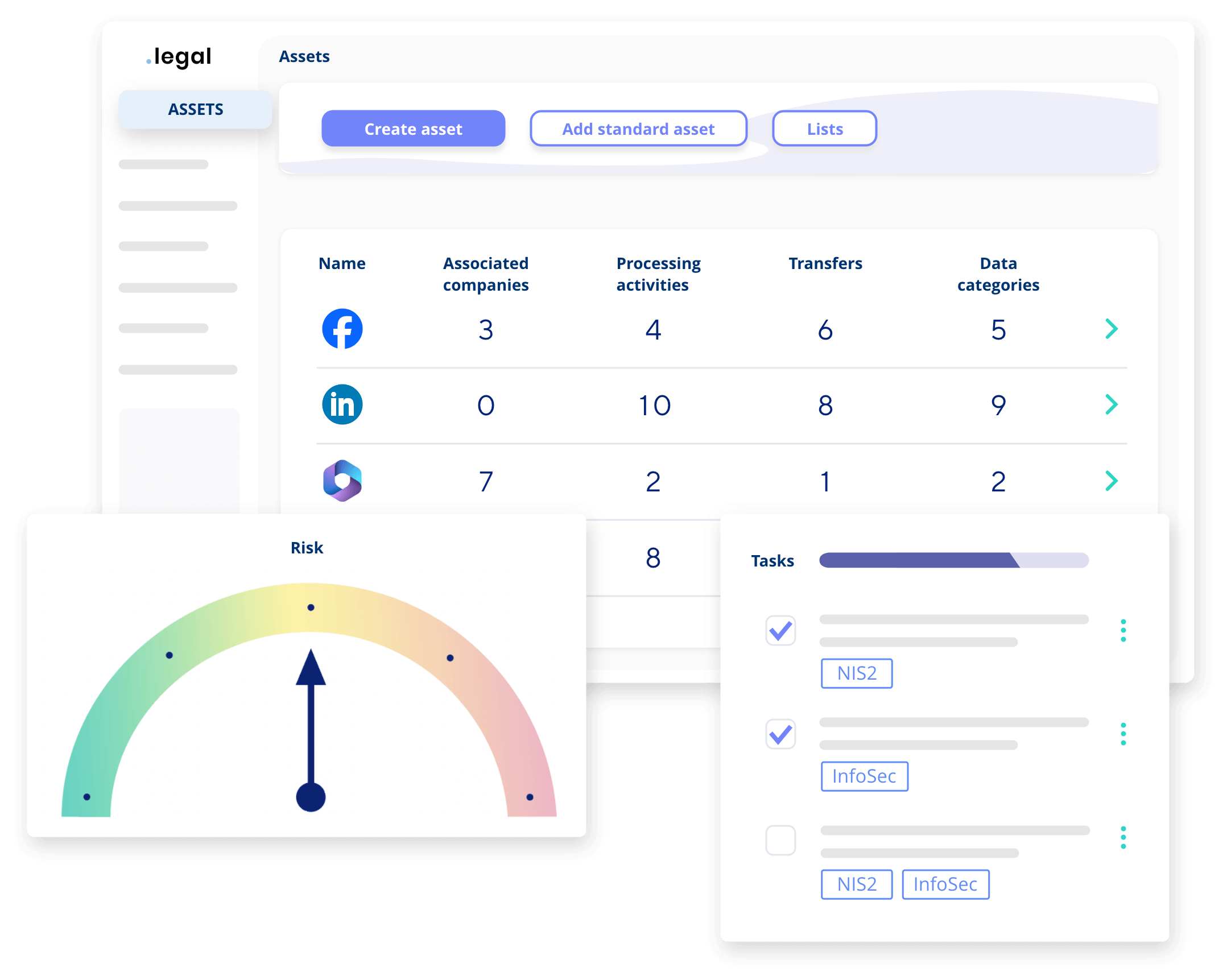
Key Features for Seamless InfoSec and CyberSec Compliance
We’ve designed the platform with a strong focus on key features that enhance your InfoSec and CyberSec compliance efforts. From intuitive navigation to integrated governance capabilities, our platform provides everything you need in a user-friendly environment. These features ensure you stay compliant while maintaining a clear, organised overview of your security landscape.
Slide through some of the main modules here.
-
Data Mapping: Easily visualise and map out your information systems and assets.
-
Risk Management: Proactively identify, assess, and mitigate risks in line with regulatory standards.
-
Standard Compliance Activities: Automate tasks for common compliance frameworks, including NIS2 and ISO 27001.
-
Incident Log: Track and document security incidents to ensure proper responses and reporting.
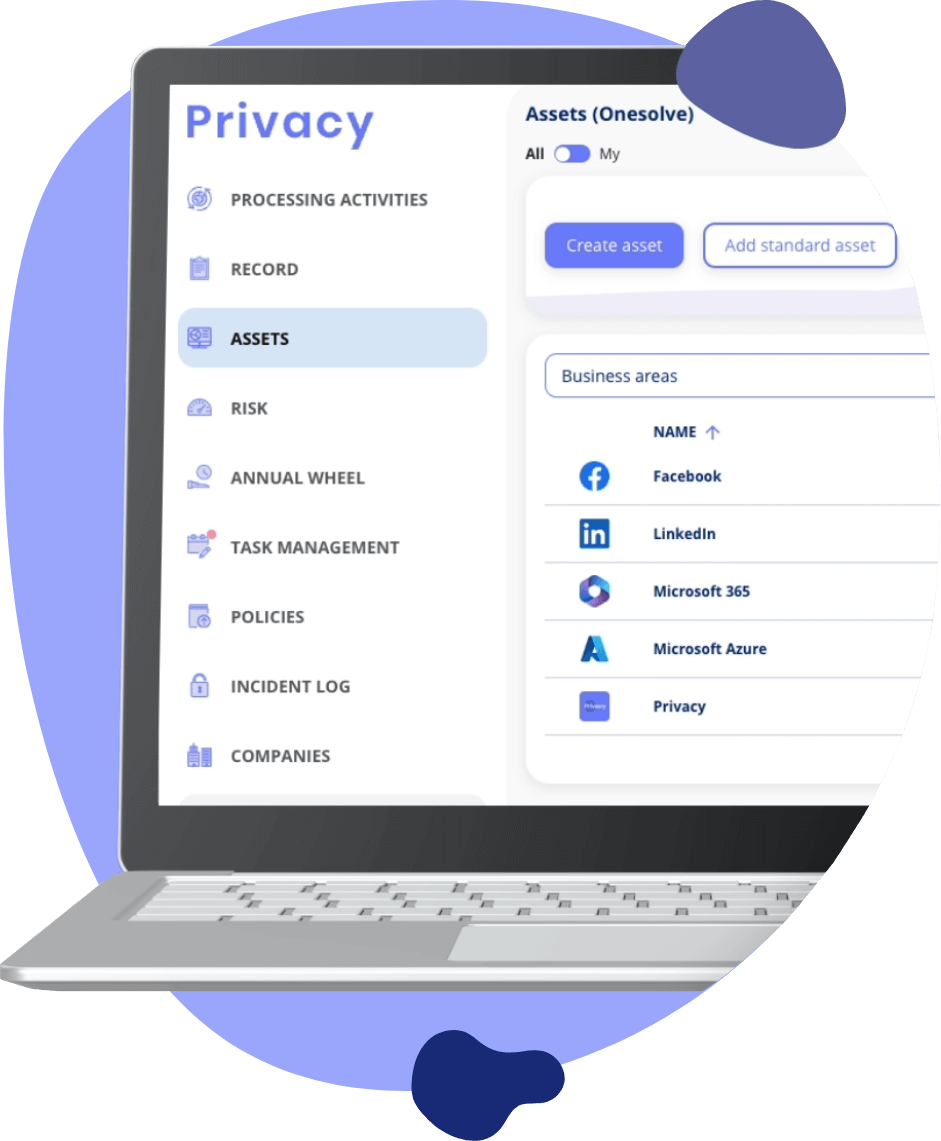
Complete Overview: Your IT Security Landscape with data mapping
Get a clear overview of your IT security compliance. Our ISMS module provides integrated features for managing your compliance. Both within InfoSec and Cyber. Simplifying complex data into actionable insights.
-
Integrated Overview: Centralise your IT systems and asset management.
-
Actionable Insights: Simplify complex data for informed decision-making.
-
Comprehensive Management: Handle all information security and cybersecurity compliance in one place.
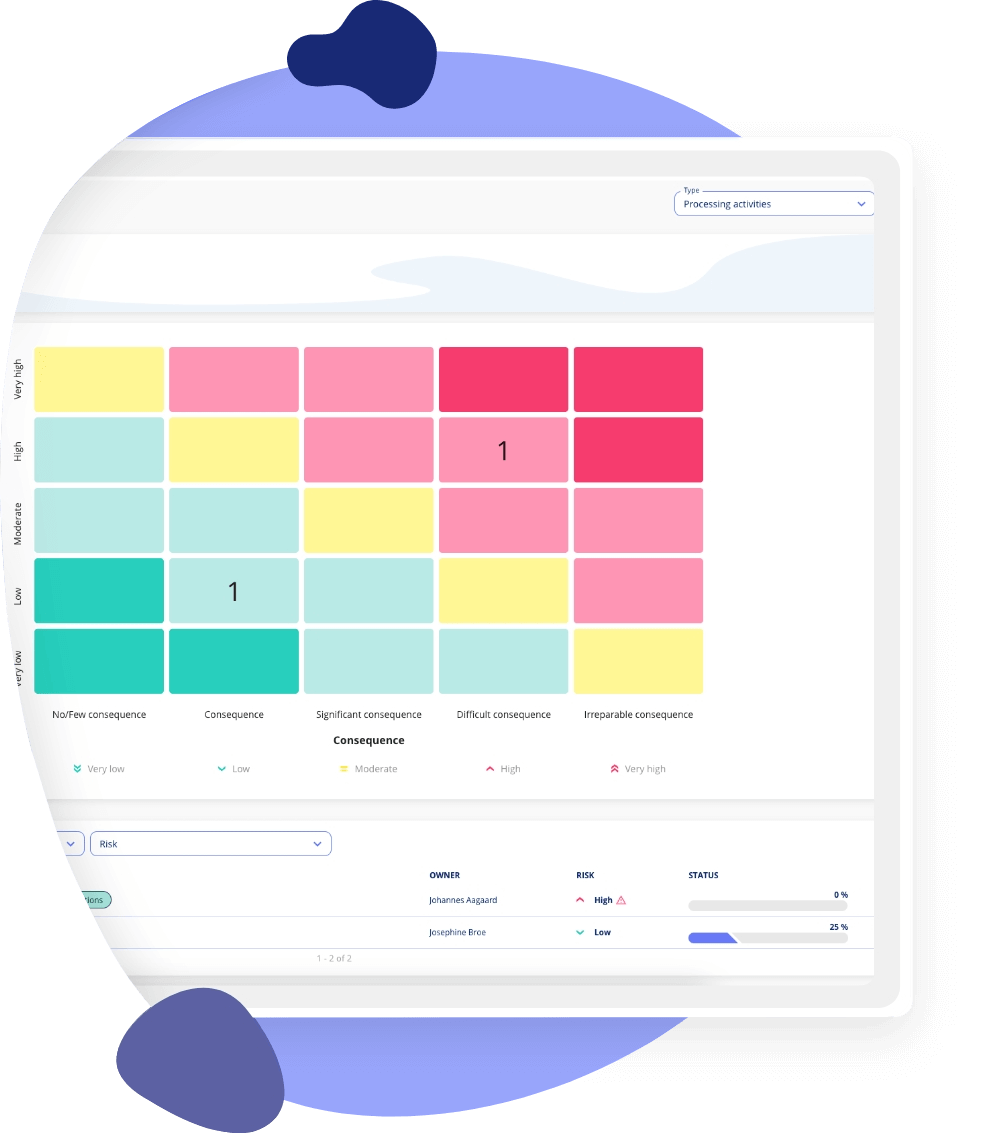
Effective Risk Assessment: Security and Compliance from Every Angle
Navigate through the complexities of IT security with our comprehensive risk assessment tools. Our module enables you to evaluate risks from both IT and cybersecurity perspectives. This helps you to ensure thorough protection.
-
Dual Perspective: Assess risks from IT and cybersecurity viewpoints.
-
Thorough Protection: Identify and mitigate potential vulnerabilities.
-
Compliance Assurance: Stay aligned with current security regulations.
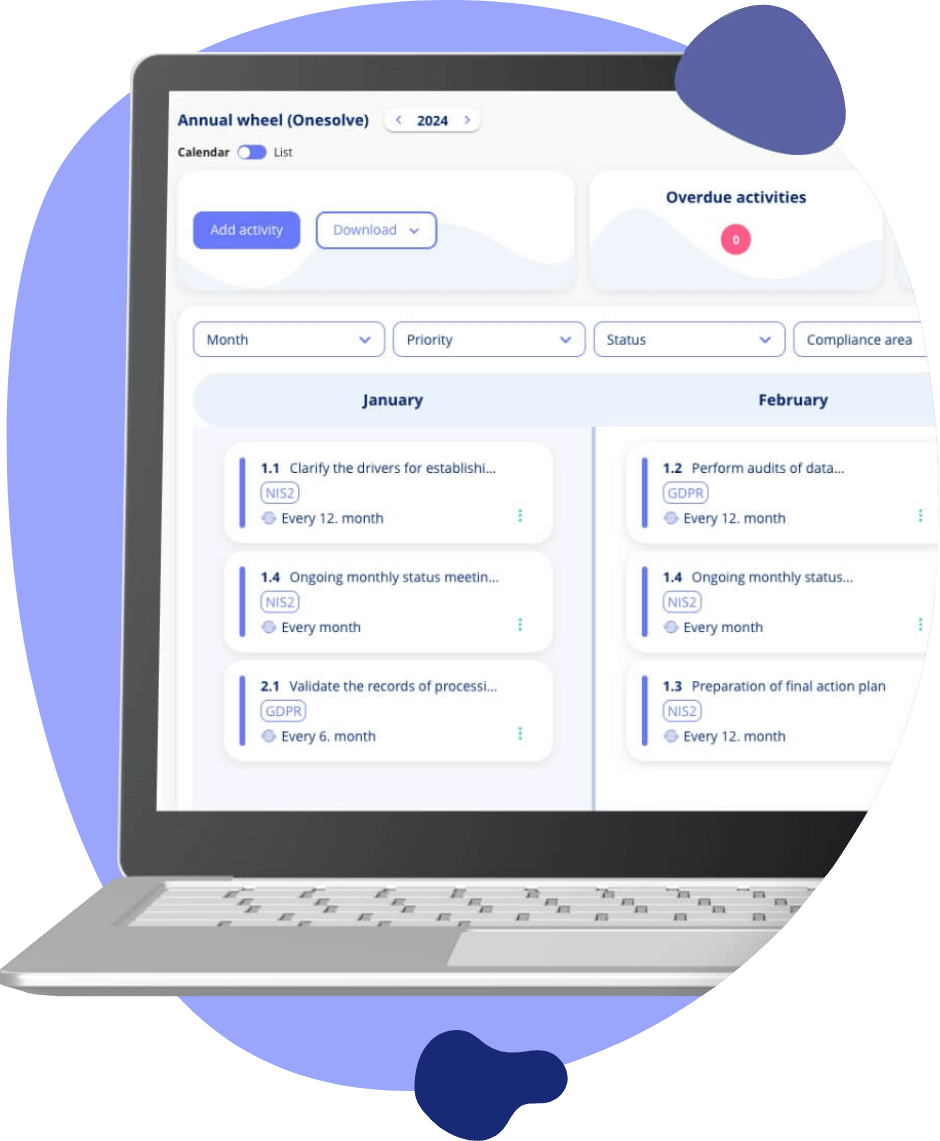
Plan your Compliance Task Management: Tailored to Your Needs
Customise your compliance planning with our adaptable task management. This feature allows for the scheduling of various compliance-related activities. Making compliance management more structured and less overwhelming.
-
Customisable Planning: Tailor your compliance schedule.
-
Structured Management: Organise compliance tasks effectively.
-
Diverse Use-cases: Adapt the task management for various compliance areas.
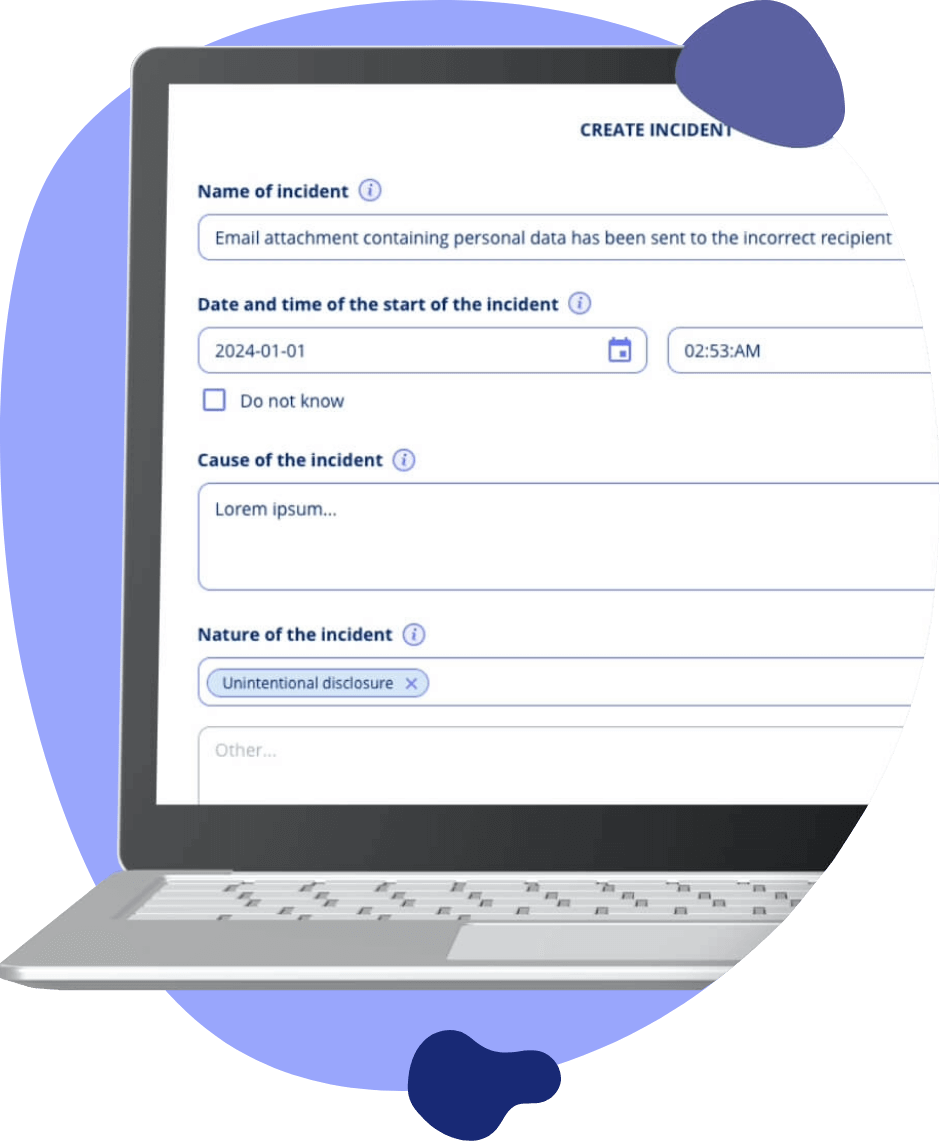
Incident Log and Risk Management: Create and Monitor with Precision
Maintain a detailed incident log and manage risks effectively with our module. If the incident happens, get an overview of all incidents and when they occurred. Make sure to meet deadlines for reporting to involved parties and regulators.
-
Detailed Incident Logging: Record and track security incidents accurately.
-
Meet deadlines: Identify incidents and inform relevant parties.
-
Historical Tracking: Utilise versioning for a chronological overview.
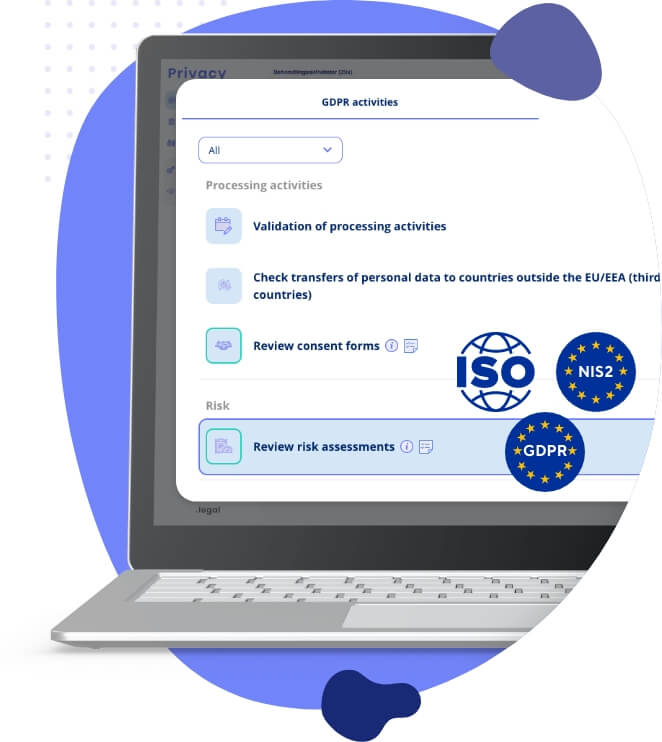
Access Ready-Made Templates and Best Practices for NIS2 and ISO Standards
Leverage our comprehensive library of templates and best practices to streamline your cybersecurity and information security processes. Whether you’re working with NIS2 or ISO27000 standards, our platform gives you a head start with proven strategies that are industry-approved. From risk assessments to incident management, our resources help you maintain compliance and boost efficiency in your operations.
-
Resource Library: Utilise a wide selection of templates and guidelines tailored to NIS2 and ISO27000 standards.
-
Proven Strategies: Implement industry-leading cybersecurity practices with ease.
-
Efficiency Boost: Save time and ensure accuracy by using ready-to-deploy templates.
See How Others Have Transformed Their Compliance
-
Michael Berner Lawyer, Lægeforeningen.legal has been the right choice for us. .legal are professional and welcoming with skilled employees.
-
Tinna Schultz HR manager, Min By MediaIt just works! It is so easy and user-friendly, and the overview of processing activities is brilliant.
-
Mikkel Friis Rossa Partner, Bech-Bruun.legal's team has consistently demonstrated a commitment to innovation while being responsive to the needs of our mutual clients.
-
Kaspar Rochholz GDPR coordinator, DMJX.legal has really understood what it means to create a user-friendly and efficient solution. Privacy is an attractive product compared to price and functionality.
-
Julie Lundkvist Andreasen Lawyer and Head of Customer Service at Axel Kaufmann ApS.legal continuously update the platform to ensure their customers always remain compliant. In our view, any other choice would be a downgrade.
-
Nanna Rodian Christensen HR & Operational Manager, Molecule ConsultancyFirstly, it means that not all the work is in one place (me), and secondly, that the understanding of GDPR is implemented throughout the organisation.
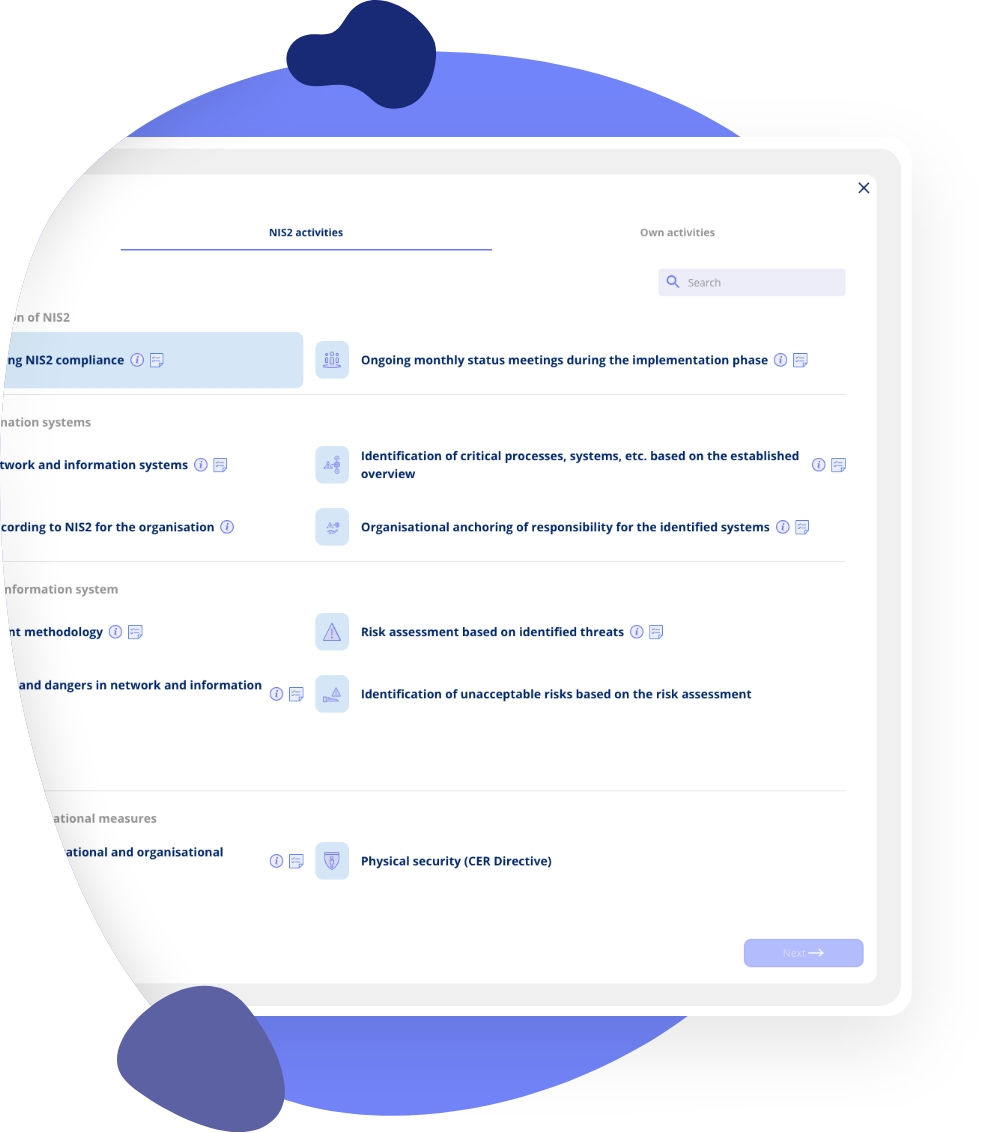
Meet NIS2 Standards with Predefined Tasks and Threat Awareness
Our platform includes predefined tasks and a clear understanding of threat landscapes, helping you meet NIS2 regulatory requirements with confidence. You’ll have access to structured workflows that guide you through compliance activities, ensuring your organization stays protected from cyber threats and meets the evolving demands of cybersecurity regulations.
-
Regulatory Compliance: Align your security practices with NIS2 standards.
-
Predefined Tasks: Follow structured, step-by-step tasks to comply with NIS2 requirements.
-
Threat Awareness: Stay up-to-date on the latest cybersecurity risks and threat landscapes.
Sign up for Information Security today
Get started for free and upgrade to a paid plan when and if you want.
No commitment - Unlimited time on free plan - No credit card needed

Why Our Platform Stands Out
Our platform is built with one central mission: to make compliance intuitive, efficient, and accessible for everyone—whether you’re an expert or not. We believe that a user-friendly interface is crucial for enabling all team members to contribute their knowledge effectively. Even those without deep expertise in GDPR or Information Security can easily navigate the platform, document their processes, and comply with standards.
Smart Reminders and Broader Compliance Management
Our platform doesn’t just help you stay compliant—it actively works with you. With built-in reminders and notifications, it ensures that nothing slips through the cracks. If you’re using both the GDPR and Information Security modules, you’ll unlock even greater value. The natural synergy between these areas means that you can streamline your processes, reducing the back-and-forth between your legal and IT departments. By automating basic tasks and guiding users through compliance processes, the platform allows your team to focus their energy on higher-priority issues.
A Complete Compliance Experience with Dedicated Support
We’re committed to delivering more than just software. Your experience with our platform includes onboarding and ongoing support, ensuring that you’re getting the most out of our tools. Whether you need assistance in setting up or want to tailor the platform to your specific needs, we’re here to help every step of the way. With our dedicated Customer Success team, you can be confident that the platform is working for you, not the other way around.
-
User-friendly Modules
Our features are designed with simplicity in mind, giving you the functionality needed to easily complete your tasks without the complexity.
-
Automated Flows
Let our platform take care of the repetitive tasks. With automated flows, you’ll avoid double registrations and save valuable time.
-
Secure Platform
Read moreWhen you choose a platform to support your Information Security compliance, it comes with high expectations for security. We meet those expectations by adhering to the strictest IT security and data protection standards, ensuring that your data remains secure at all times.
-
A Trustworthy Vendor
Read moreWe value the relationship we build with you. From exceptional onboarding and ongoing support to sharing best practices, we’re here to ensure you feel secure in using our platform.
Product Updates
-
01:38
Oct 4th, 2024
-
01:18
Sep 27th, 2024
-
01:58
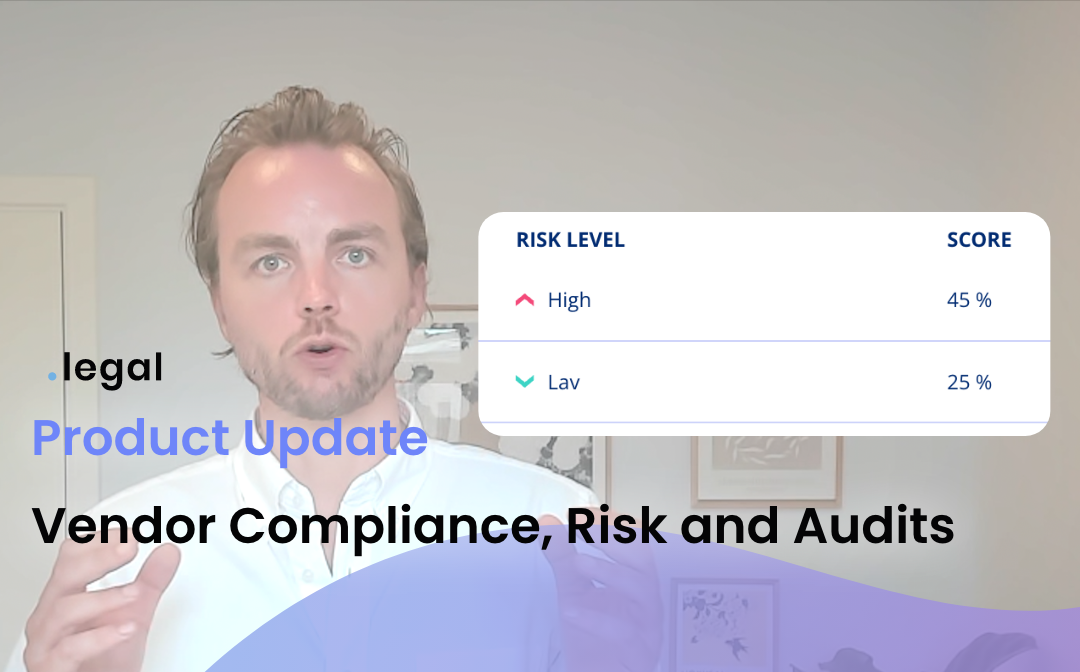
Aug 6th, 2024
-
02:26

May 21th, 2024
-
01:54
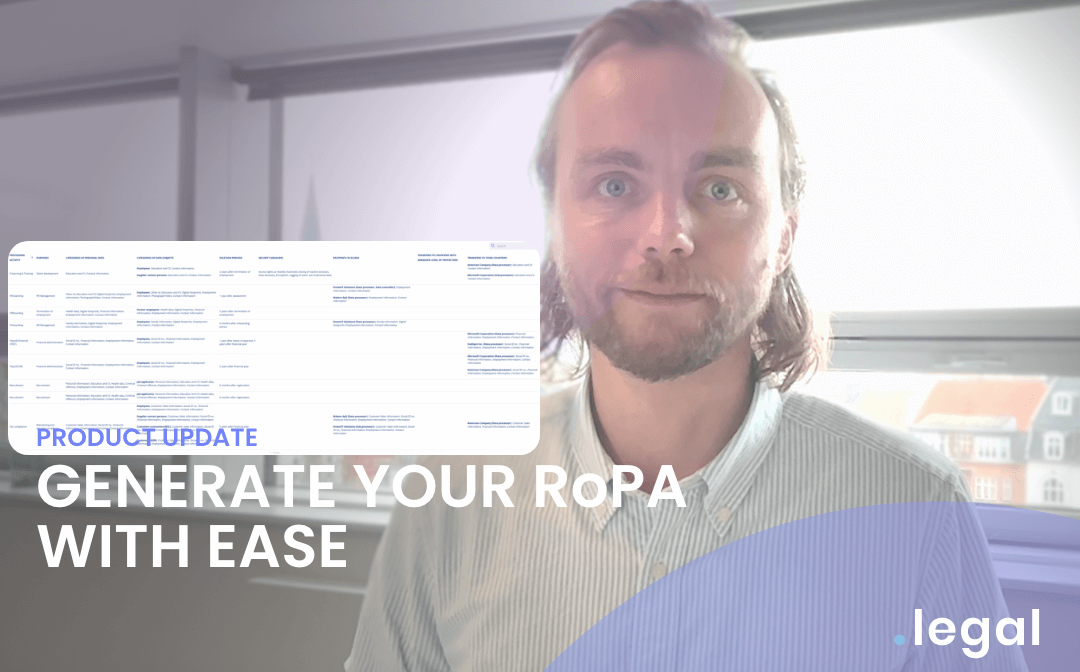
May 13th, 2024
-
02:28
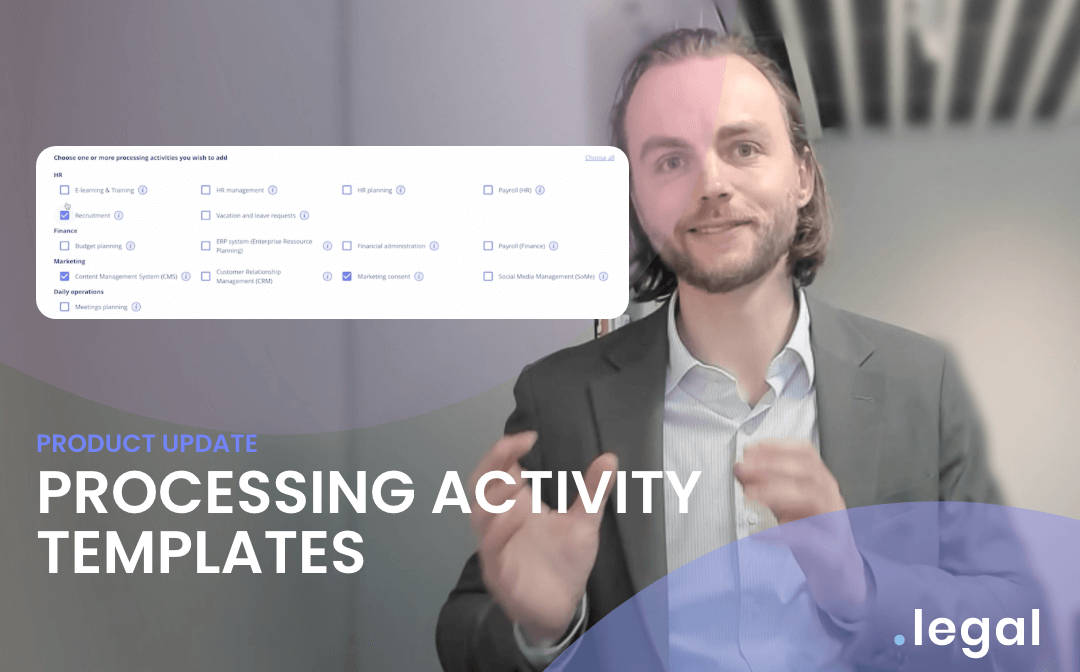
April 11th, 2024
-
02:37
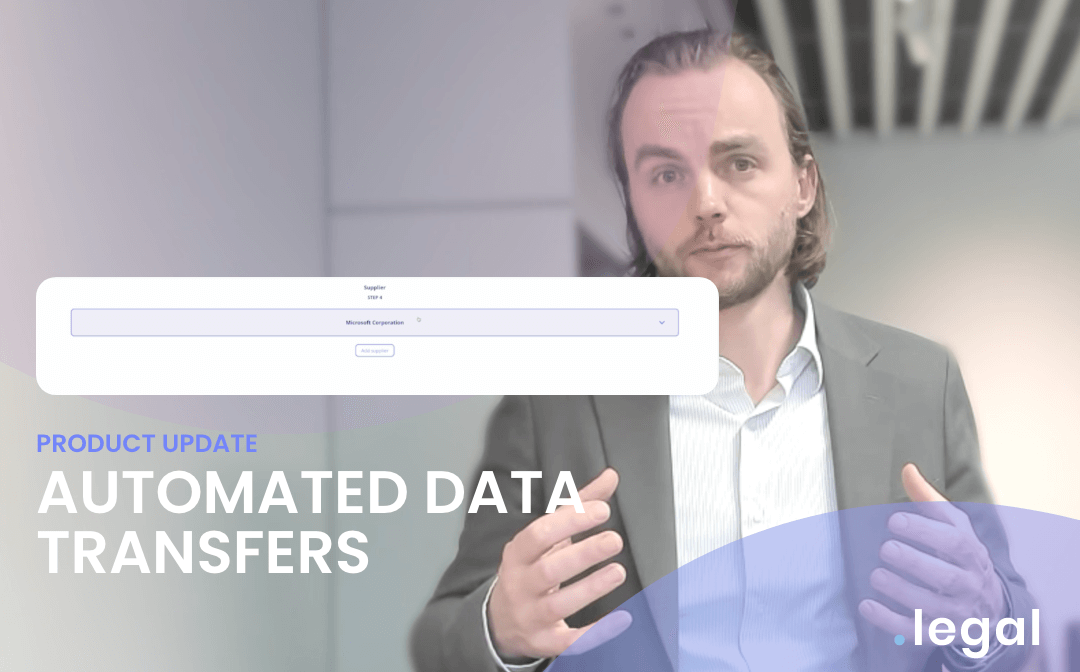
April 11th, 2024
-
01:38

April 9th, 2024
-
02:22
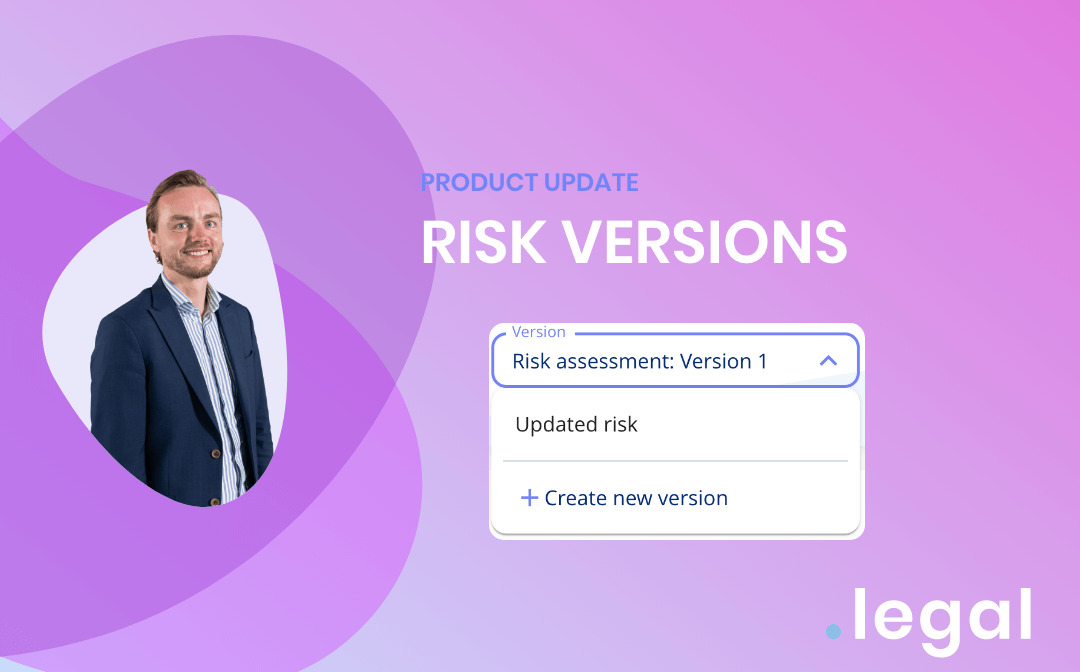
February 20th, 2024
-
02:11
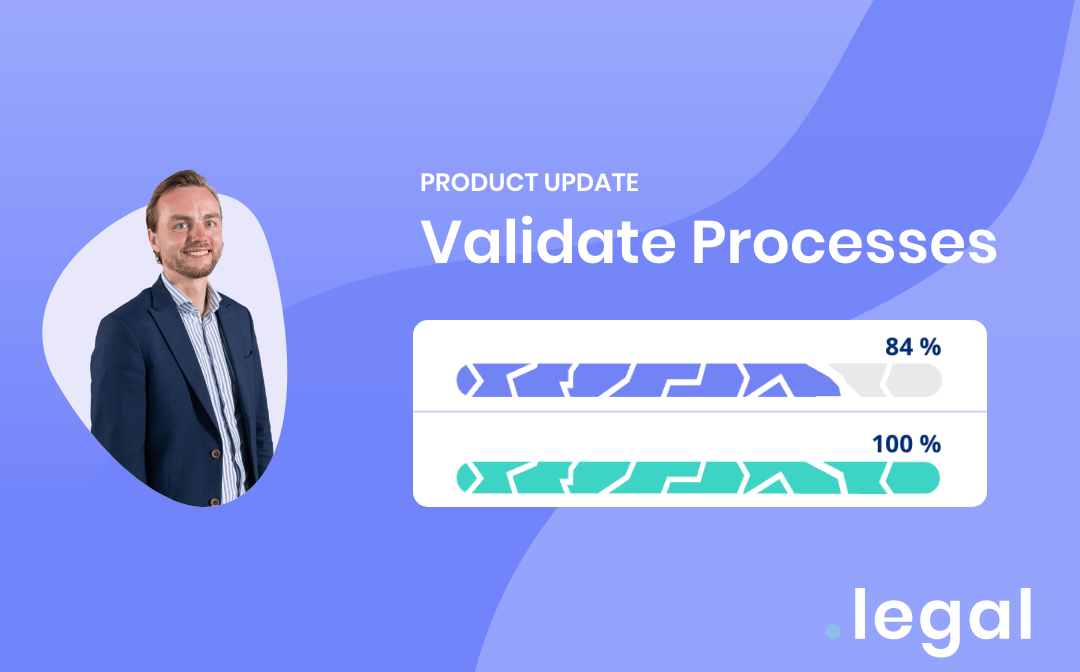
February 20th, 2024
-
02:14

February 20th, 2024
-
01:34
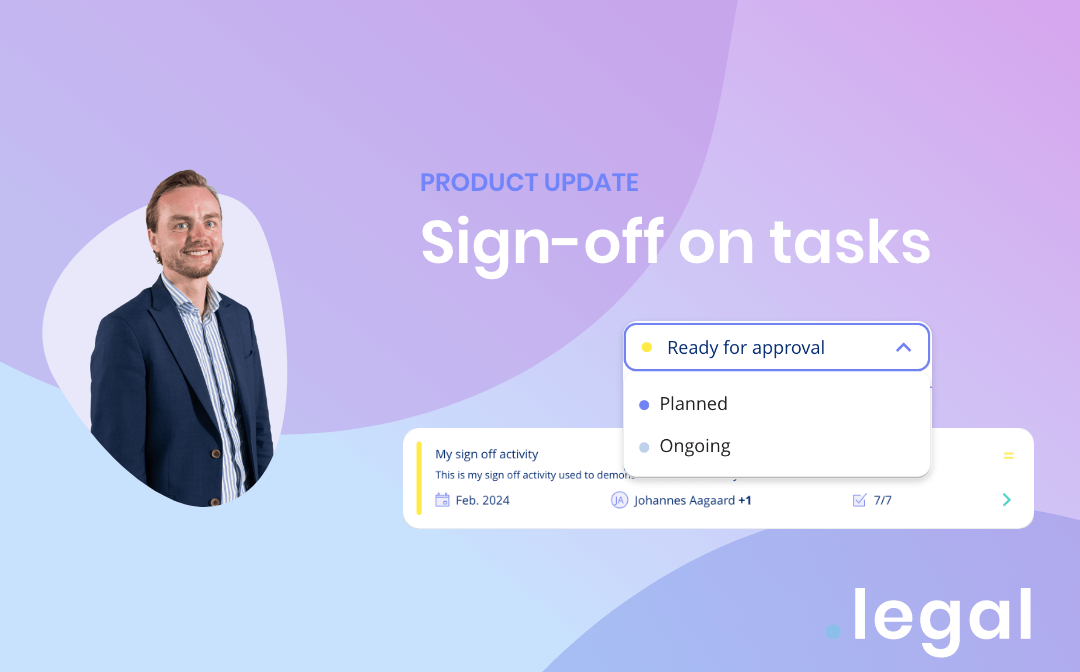
February 14th, 2024
-
02:13

February 14th, 2024
-
01:59
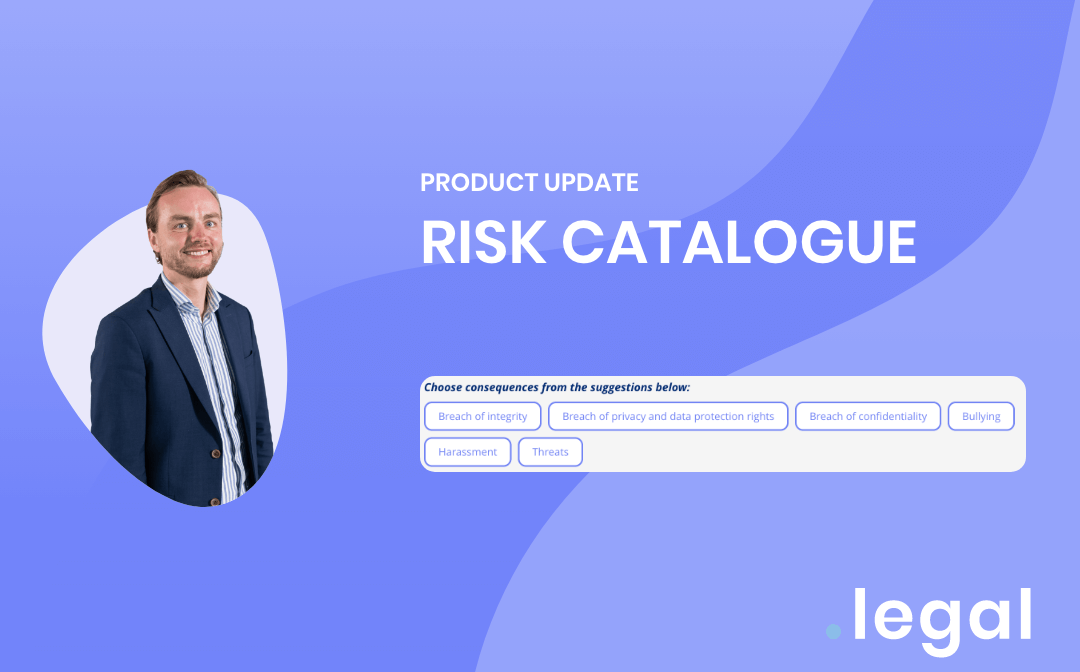
February 14th, 2024
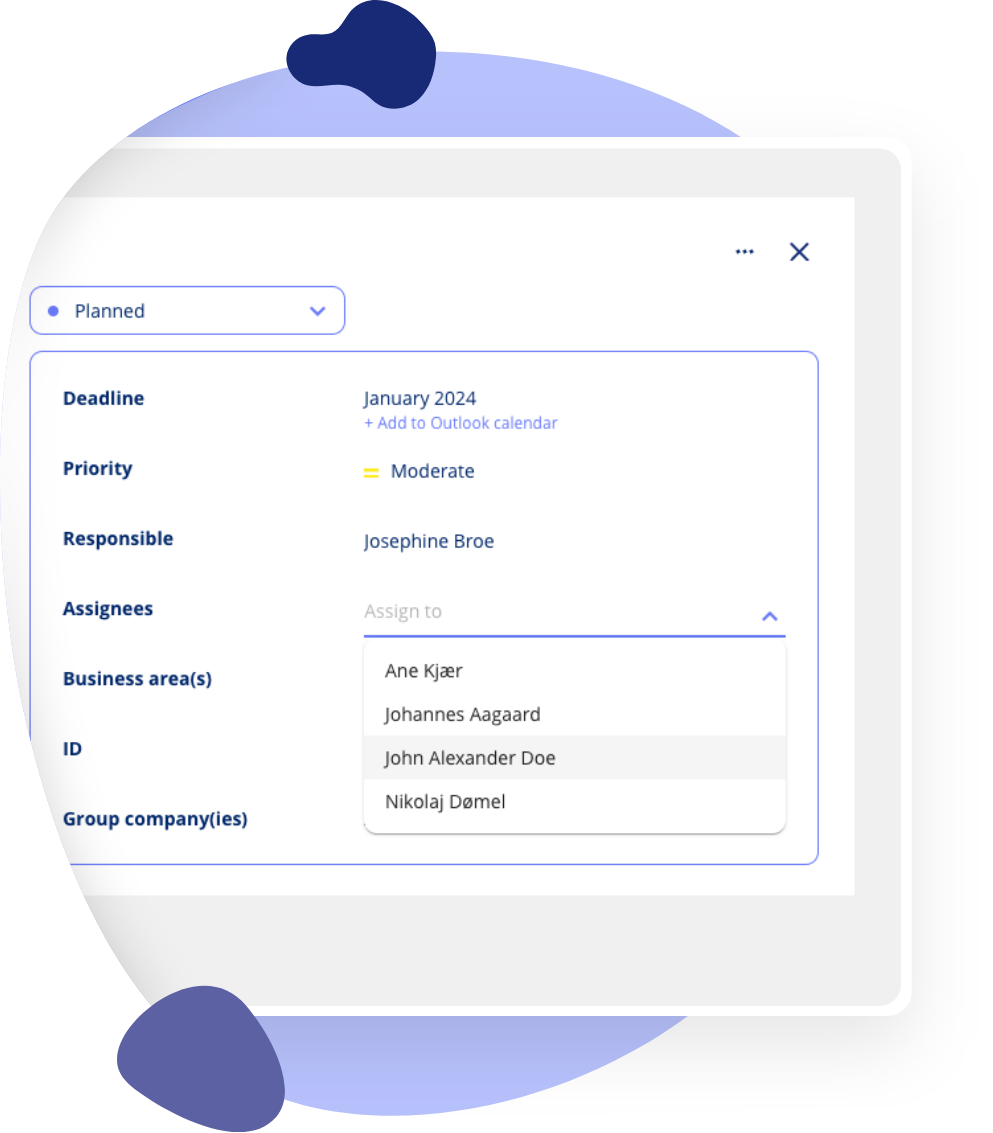
Delegation Made Easy: Collaborate and Notifications
Enhance team collaboration with task delegation and real-time notifications. Our module streamlines communication. And ensures everyone is on track with their compliance responsibilities.
-
Streamlined Collaboration: Delegate tasks efficiently.
-
Real-time Updates: Stay informed with instant notifications.
-
Responsibility Tracking: Ensure accountability in compliance tasks.

Document IT Security and Cybersecurity: Store Policies and Procedures
Safeguard your IT security and cybersecurity documents in our policy library. Easily upload and manage all relevant policies and procedures. Ensuring they are accessible to relevant colleagues and up-to-date.
-
Secure Storage: Keep your IT security documents safe and organized.
-
Easy Management: Upload and update policies effortlessly.
-
Accessibility: Ensure important documents are readily available.
Learn more Read more about InfoSec

ONBOARDING Easy to get started
We help you get started with using Privacy. Our onboarding specialists ensure that Privacy is set up for you and, in collaboration with you, we create the first processing activities, so that you are well prepared to continue the documentation work afterwards.
If you have already prepared processing activities in e.g. Excel or Word, you are welcome to send these in advance, because then we will start from this in the onboarding process.


.jpg)


.jpeg)

.jpg)
.jpg)



.jpg)

-1.png)



.jpeg)








.jpg)

Info
.legal A/S
hello@dotlegal.com
+45 7027 0127
VAT-no: DK40888888
Support
support@dotlegal.com
+45 7027 0127
Need help?
Let me help you get started

+45 7027 0127 and I'll get you started
.legal is not a law firm and is therefore not under the supervision of the Bar Council.